OSI Model: A Detailed Overview with Attack Vectors
NetworkingA conceptual framework known as the OSI Model (Open Systems Interconnection Model) divides the operations of a computer or communication system into seven separate levels. Every layer interacts with the layers immediately above and below it and has distinct duties. Network experts need to understand the OSI model since it offers a clear picture of data flow within a network and helps in network diagnosis and security against any threats.
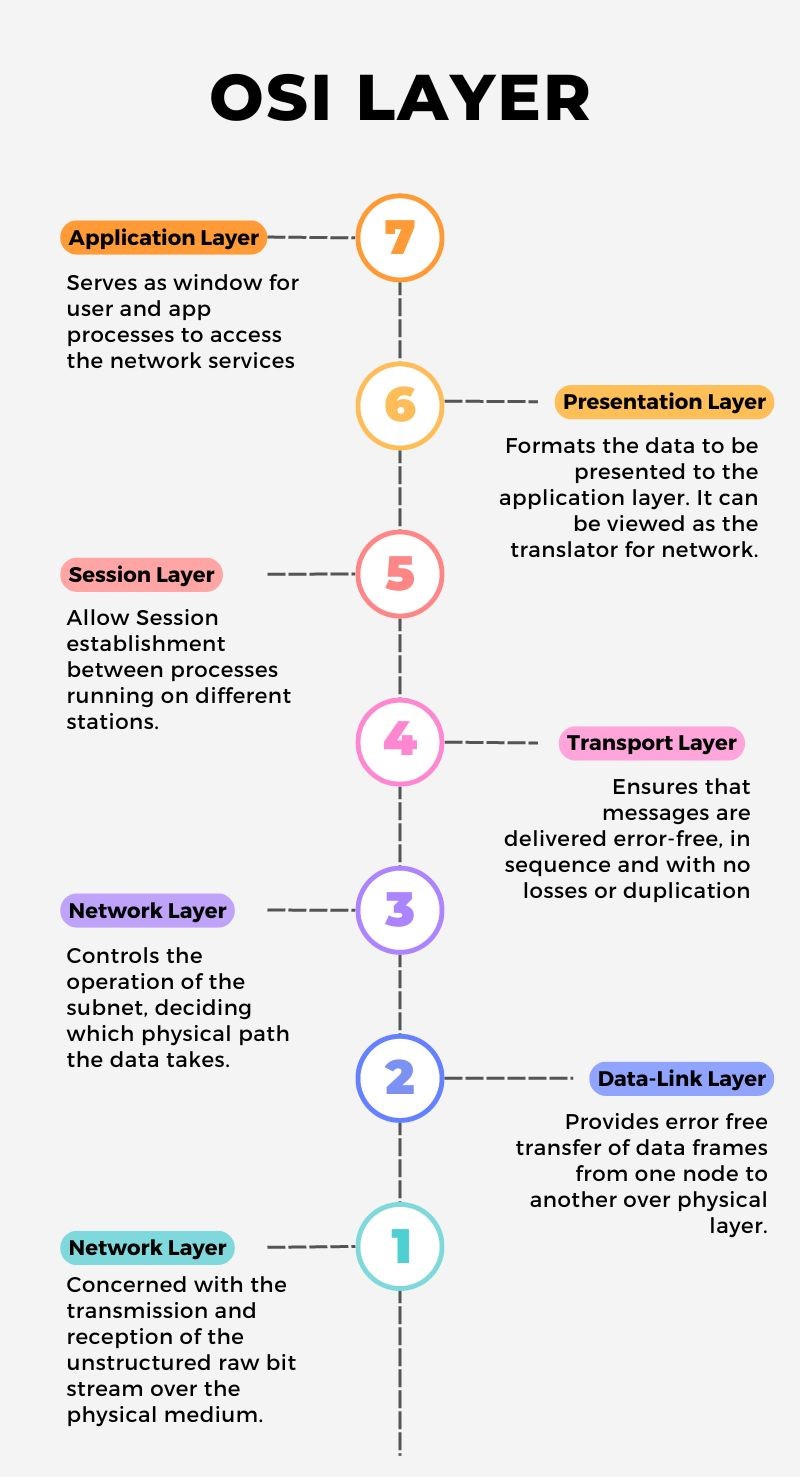
Overview of the OSI Model Layers:
The OSI model has seven layers, each representing a specific function within the communication process:
- Layer 1: Physical Layer
- Layer 2: Data Link Layer
- Layer 3: Network Layer
- Layer 4: Transport Layer
- Layer 5: Session Layer
- Layer 6: Presentation Layer
- Layer 7: Application Layer
First Layer: The Physical Layer
Function: Raw bitstreams (0s and 1s) are transmitted via physical media like cables, radio frequencies, or fiber optics by the Physical Layer. It deals with electrical impulses, network interface cards (NICs), cables, switches, and other hardware components.
Examples: Ethernet cables, fiber optics, and wireless signals.
Attack Vectors:
Physical Tampering: Unauthorized access to physical network devices, such as cutting cables or tapping lines, can cause communication to be disrupted or manipulated.
Eavesdropping: Via physical network infrastructure penetration techniques like wiretapping, attackers may be able to intercept data.
Jamming is the deliberate creation of interference in wireless networks to hinder or completely prevent transmission.
Second Layer:Data Link Layer
Function: The Data Link Layer manages data frames between neighboring network nodes, error detection, and node-to-node data transfer. In addition, it controls physical media access and assigns MAC (Media Access Control) addresses to hardware.
Examples: Ethernet, Wi-Fi (IEEE 802.11), and PPP (Point-to-Point Protocol).
Attack Vectors:
MAC Flooding: This technique involves flooding a switch with fake MAC addresses, which makes it function like a hub and route all traffic to all ports, leaving the attacker with the opportunity to intercept it.
ARP spoofing: The attacker links their MAC address to the IP address of another site by sending fictitious ARP (Address Resolution Protocol) packets, which enables them to intercept, alter, or halt data in transit.
VLAN Hopping: To access network segments that would otherwise be segregated, an attacker transmits packets to a different VLAN than the one that has been allotted.
Third Layer: Network Layer
Function: Oversees data packet forwarding and routing between devices connected to various networks. Device identification is done using IP addresses.
Examples include ICMP (Internet Control Message Protocol) and Internet Protocol (IP).
Attack Vectors:
IP Spoofing: Using a faked source address to send packets in order to get around security controls.
Routing attacks: Redirecting traffic by tampering with routing protocols, such as BGP hijacking.
Sniffing packets on the network to retrieve private data is known as packet sniffing.
Fourth Layer: Transport Layer
Function: The Transport Layer gives the higher layers efficient data transport services. It oversees error correction, flow control, and end-to-end communication. At this layer, protocols such as UDP (User Datagram Protocol) and TCP (Transmission Control Protocol) function.
Examples: TCP, UDP, SCTP (Stream Control Transmission Protocol).
Attack Vectors:
TCP SYN Flood: The attacker overwhelms the target’s ability to handle new connections by sending an overwhelming volume of TCP/SYN packets, which causes a denial of service.
Session Hijacking: By guessing the TCP sequence numbers and inserting malicious data, the attacker gains control of a valid TCP session.
UDP Flooding: An attacker uses network resources and bandwidth by flooding a target machine with enormous amounts of UDP packets sent to random ports.
Fifth Layer: Session Layer
Function: The computer conversations, or sessions, are managed and controlled by the session layer. Between programs, it creates, maintains, and breaks connections.
Examples: NetBIOS, RPC (Remote Procedure Call).
Attack Vectors:
Session Hijacking: Following authentication, an attacker seizes control of a user’s session, granting unauthorized access to the program or service.
Session Fixation: After the user authenticates, the attacker uses the session ID to carry out malicious actions by setting it to a known value.
The man in the Middle-attacks: Communication between two parties is intercepted and altered.
Session Replay: The technique of impersonating a user by capturing and reusing valid session tokens.
Sixth Layer: Presentation Layer
Function: Data translation, encryption, and compression are handled by the Presentation Layer. It guarantees that information is shown in a way that the application layer can understand.
Examples: SSL/TLS (for encryption), JPEG, ASCII.
Attack Vector:
SSL/TLS Attacks: Data can be intercepted in an unencrypted form using attacks like SSL stripping or taking advantage of holes in the SSL/TLS protocols.
Man-in-the-Middle (MitM) attacks: These occur when an attacker eavesdrops on and modifies data being transmitted between two parties, frequently by breaking the encryption.
Data manipulation: Modifying data in order to introduce vulnerabilities before presenting it to the application.
Injection Attacks: When malicious code (such as SQL injection) is inserted into data that is being processed.
Seventh Layer:Application Layer
Function: The Application Layer delivers network services including file transfers, web browsing, and email by interacting directly with end-user applications. This layer contains protocols including DNS, SMTP, FTP, and HTTP.
Examples: SSL/TLS (for encryption), JPEG, ASCII.
Attack Vectors:
Phishing: Through phony emails or websites that appear authentic, attackers deceive victims into disclosing personal information.
SQL Injection: To alter or steal data from a database, attackers inject malicious SQL code into a web application.
Cross-Site Scripting (XSS): When malicious scripts are injected into pages that other users view, it gives attackers the ability to deface websites or steal session cookies.
DNS spoofing: The attacker sends bogus DNS answers or tampers with the DNS cache to reroute visitors to malicious websites.
Conclusion:
Understanding how data moves across a network can be done in layers thanks to the OSI model, which covers everything from the actual bit transmission to user interactions at the application level.
Every layer in the OSI model has a unique set of duties and possible weak points.
Through awareness of the distinct attack vectors linked to every tier, security experts may establish more efficient defenses to safeguard network infrastructure and information.

Skilled and motivated penetration tester with a strong foundation in cybersecurity fundamentals and a passion for learning and growing.